In the ever-evolving landscape of networking technologies, Multiprotocol Label Switching (MPLS) has In the ever-evolving landscape of networking technologies, Multiprotocol Label Switching (MPLS) has emerged as a crucial and versatile tool for efficiently directing data traffic across networks. MPLS brings a new level of flexibility and performance to network communication. In this article, we will explore the fundamentals of MPLS, its purpose, and its relationship with the innovative technology of Software-Defined Wide Area Networking (SD-WAN).
What is MPLS (Multiprotocol Label Switching)?
Before we delve into the specifics of MPLS, it’s important to understand the journey of data across the internet. Whenever you send an email, engage in a VoIP call, or participate in video conferencing, the information is broken down into packets, commonly known as IP packets, which travel from one router to another until they reach their intended destination. At each router, a decision must be made about how to forward the packet, a process that relies on intricate routing tables. This decision-making is required at every juncture in the packet’s path, potentially leading to inefficiencies that can degrade performance for end-users and affect the overall network within an organization. MPLS offers a solution that can enhance network efficiency and elevate the user experience by streamlining this process.
MPLS Definition
Multiprotocol Label Switching (MPLS) is a protocol-agnostic, packet-forwarding technology designed to improve the speed and efficiency of data traffic flow within a network. Unlike traditional routing protocols that make forwarding decisions based on IP addresses, MPLS utilizes labels to determine the most efficient path for forwarding packets.
At its core, MPLS adds a label to each data packet’s header as it enters the network. This “label” contains information that directs the packet along a predetermined path through the network. Instead of routers analyzing the packet’s destination IP address at each hop, they simply read the label, allowing for faster and more streamlined packet forwarding.
MPLS Network
An MPLS network is considered to operate at OSI layer “2.5”, below the network layer (layer 3) and above the data link layer (layer 2) within the OSI seven-layer framework. The Data Link Layer (Layer 2) handles the transportation of IP packets across local area networks (LANs) or point-to-point wide area networks (WANs). On the other hand, the Network Layer (Layer 3) employs internet-wide addressing and routing through IP protocols. MPLS strategically occupies the space between these two layers, introducing supplementary features to facilitate efficient data transport across the network.
The FS S8550 series switches support advanced features of MPLS, including LDP, MPLS-L2VPN, and MPLS-L3VPN. To enable these advanced MPLS features, the LIC-FIX-MA license is required. These switches are designed to provide high reliability and security, making them suitable for scenarios that require compliance with the MPLS protocol. If you want to know more about MPLS switches, please read fs.com.
What is MPLS Used for?
Traffic Engineering
One of the primary purposes of MPLS is to enhance traffic engineering within a network. By using labels, MPLS enables network operators to establish specific paths for different types of traffic. This granular control over routing paths enhances network performance and ensures optimal utilization of network resources.
Quality of Service (QoS)
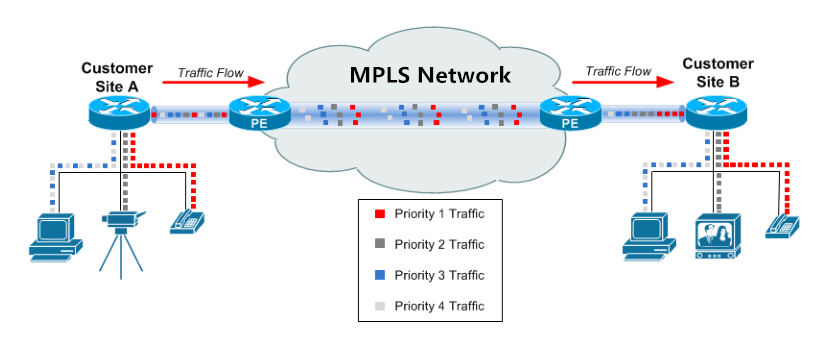
MPLS facilitates effective Quality of Service (QoS) implementation. Network operators can prioritize certain types of traffic by assigning different labels, ensuring that critical applications receive the necessary bandwidth and low latency. This makes MPLS particularly valuable for applications sensitive to delays, such as voice and video communication.
Scalability
MPLS enhances network scalability by simplifying the routing process. Traditional routing tables can become complex and unwieldy, impacting performance as the network grows. MPLS simplifies the decision-making process by relying on labels, making it more scalable and efficient, especially in large and complex networks.
Traffic Segmentation and Virtual Private Networks (VPNs)
MPLS supports traffic segmentation, allowing network operators to create Virtual Private Networks (VPNs). By using labels to isolate different types of traffic, MPLS enables the creation of private, secure communication channels within a larger network. This is particularly beneficial for organizations with geographically dispersed offices or remote users.
MMPLS Integrates With SD-WAN
Integration with SD-WAN
MPLS plays a significant role in the realm of Software-Defined Wide Area Networking (SD-WAN). SD-WAN leverages the flexibility and efficiency of MPLS to enhance the management and optimization of wide-area networks. MPLS provides a reliable underlay for SD-WAN, offering secure and predictable connectivity between various network locations.
Hybrid Deployments
Many organizations adopt a hybrid approach, combining MPLS with SD-WAN to create a robust and adaptable networking infrastructure. MPLS provides the reliability and security required for mission-critical applications, while SD-WAN introduces dynamic, software-driven management for optimizing traffic across multiple paths, including MPLS, broadband internet, and other connections.
Cost Efficiency
The combination of MPLS and SD-WAN can result in cost savings for organizations. SD-WAN’s ability to intelligently route traffic based on real-time conditions allows for the dynamic utilization of cost-effective connections, such as broadband internet, while still relying on MPLS for critical and sensitive data.
Want to learn more about the pros and cons of SD-WAN and MPLS, please check SD-WAN vs MPLS: Pros and Con
Conclusion
In conclusion, Multiprotocol Label Switching (MPLS) stands as a powerful networking technology designed to enhance the efficiency, scalability, and performance of data traffic within networks. Its ability to simplify routing decisions through the use of labels brings numerous advantages, including improved traffic engineering, Quality of Service implementation, and support for secure Virtual Private Networks.
Moreover, MPLS seamlessly integrates with Software-Defined Wide Area Networking (SD-WAN), forming a dynamic and adaptable networking solution. The combination of MPLS and SD-WAN allows organizations to optimize their network infrastructure, achieving a balance between reliability, security, and cost efficiency. As the networking landscape continues to evolve, MPLS remains a foundational technology, contributing to the seamless and efficient flow of data in diverse and complex network environments.